Open Source Sensitive Data Discovery

Scroll down for pii tools.
Open source sensitive data discovery. Java jar redatasense jar database discovery d note. The secret behind spirion data platform s highly accurate sensitive data discovery software solution is our anyfind technology. Remember that on version 3 0 all configuration for data discovery is stored on database. The era of clumsy regexps is.
Quarantine delete or revoke access to exposed data. Sensitive data discovery and achieving compliance is made possible with ground lab s unique software and tools. Sensitive data discovery done right automated pii scans and data audits for maintained compliance. Search engine like tools are a niche category in data discovery.
Introducing a world without manual discovery. Sensitive data discovery identifies data that is the most at risk to exposure such as pii phi and phi. There are lots of high end products that will automate the process of data discovery but it doesn t take much effort to hunt down data yourself. Varonis automatically scans and classifies sensitive regulated information stored in file shares nas devices sharepoint and office 365.
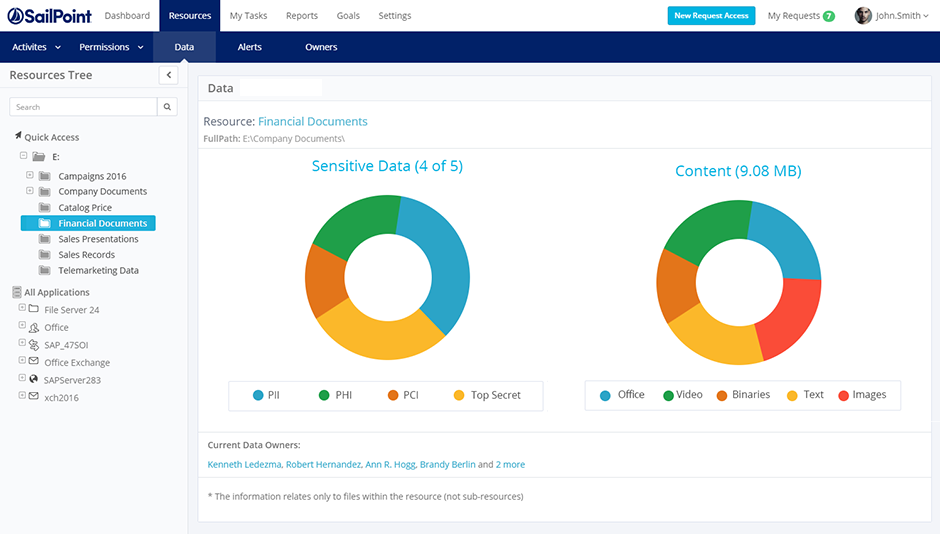
Understanding what and where sensitive information is allows you to set appropriate levels of control in your data discovery process. Data classification engine gives context around sensitive data so that you can easily identify and lock down overexposed data stale data and remediate security vulnerabilities. Track information across your network including file shares san and nas storage and sharepoint sites. Data discovery will perform an nlp scan an regex scan or dictionary scan of data in the database and return columns that have a match score greater than the value of probability threshold specified in parameters.
Check out this list of sensitive data discovery tools and choose the one that is the best fit for your organization s needs. Structured unstructured or semi structured. Pii tools comes with context sensitive ai detectors for gdpr ccpa phi pci and more. You ve got sensitive data.
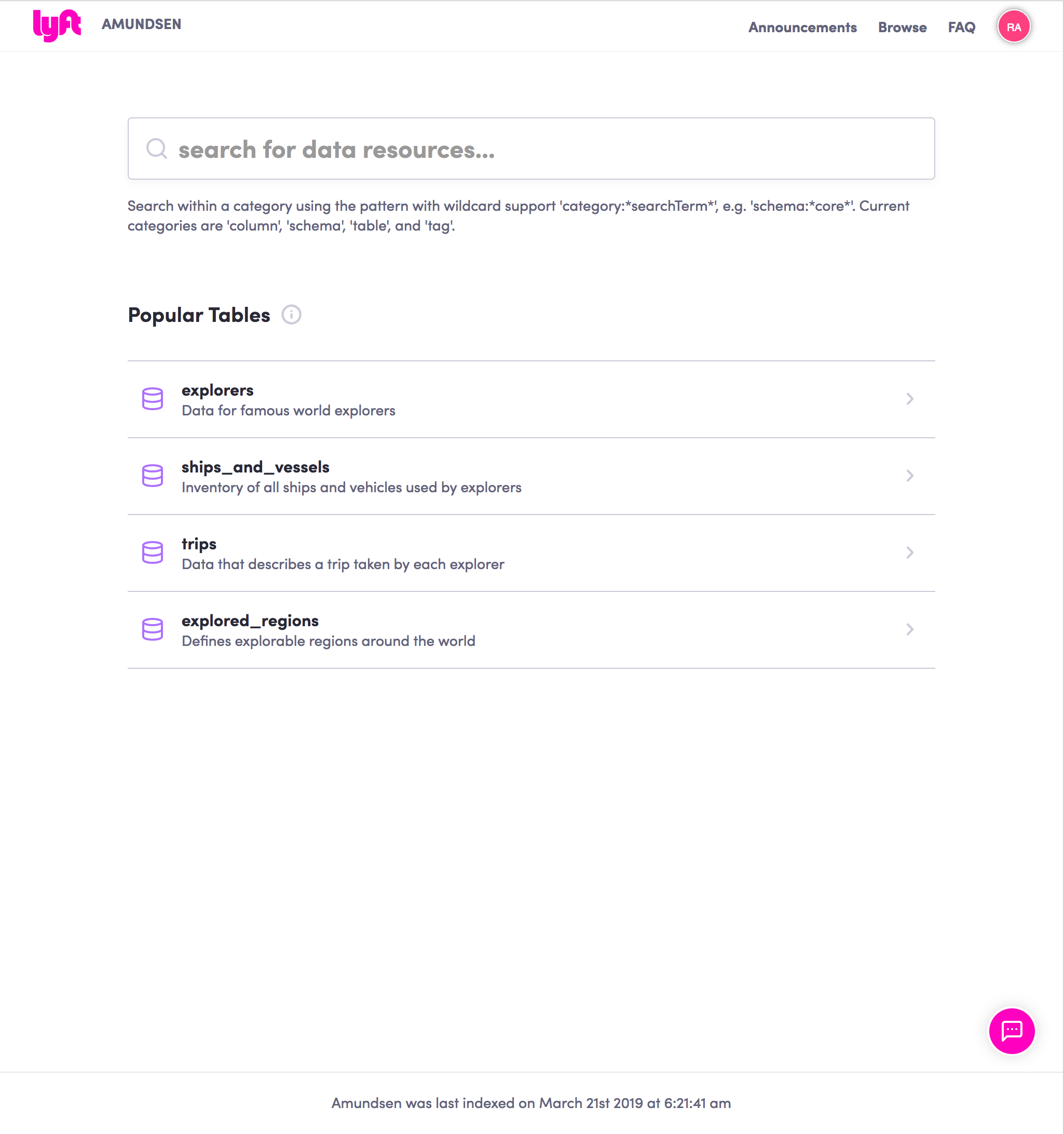
But it can also be customized to have custom data classifiers. They re specifically for performing keyword searches of large collections of files and they feature an interface similar to that of web search engines such as google and bing. Trust the companies that trust us. Visual data interaction tools make up the bulk of the data discovery market and frequently data discovery is used as a synonym for business analytics via interactive visualizations.
Remediate compliance breaches in real time. Kogni is capable of detecting your sensitive data from any kind of data source.